Pages: 288
Publisher: Amazon CreateSpace
ISBN: 978-1500966836
“Collision Domain” is a thriller about the murder spree of a sociopath who uses state-of-the-art computer hacks to kill his victims.
“A successful manager dying in an unlikely car accident presents police with a mystery: nothing hints at outside influence, intoxication or human error. Just as the case is about to be closed, a family is killed in a similar accident. Not believing in coincidence, lead investigator Nathaniel Pierce soon discovers the connection between the crimes: in both cases, parts of the car’s brake control software had been remotely altered.
The increasing number of deadly cyber-incidents soon makes it clear that the hacker’s killing spree has only just begun: with each passing day, more and more people are affected. Voices demanding Internet regulations grow louder amidst the chaos and soon the case becomes a political issue. Nathaniel is teamed up with corporate security expert Eryn Veela to track down the criminal before the final line is crossed…”
Print edition: Amazon.com | Amazon.co.uk | Amazon.de
Kindle e-book: Amazon.com | Amazon.co.uk | Amazon.de
Initial idea by Ernst Piller.
Cover design by Martina Bräuner.
“Collision Domain” and Cyber-Security
The scenario of Collision Domain is based on facts. Every cyber-attack presented in this book is possible and can be executed with today’s technology.
This novel was created as part of a thesis with the goal to present today’s Internet security issues as well as a possible conceptual solution in a readily comprehensible manner. It is written for tech-savvy individuals but mostly for people who just enjoy a good thriller; we recommend you give it a try even if you are not active in the field of IT or information security.
The book consists of two parts. The larger part contains the actual story told from three unique perspectives. They provide the reader with a glimpse at the dark side of the digital domain and at how criminals exploit and abuse today’s unregulated Internet.
The second part comes in the form of a sizable appendix where we discuss each attack and its implications and present a concept for a more secure global network environment. The interested reader will find plenty of references to papers and articles discussing many of the issues in greater detail. Reading the appendix is optional and not required to enjoy the book.
Introduction
 Corporations and governments around the globe are engaged in an arms race against organized crime and often against each other. Espionage, sabotage and fraud have long since crossed the border into the digital domain. The term ‘cybercrime’, as vaguely defined as it is, is on everyone’s lips. Between 2005 and 2012, respective references in global news have gone up by about 600% [1, pp. 7].
Corporations and governments around the globe are engaged in an arms race against organized crime and often against each other. Espionage, sabotage and fraud have long since crossed the border into the digital domain. The term ‘cybercrime’, as vaguely defined as it is, is on everyone’s lips. Between 2005 and 2012, respective references in global news have gone up by about 600% [1, pp. 7].
This development is hardly surprising. Where there are people, there is crime. The Internet is no longer a pet project of a small number of freethinkers but has become an important factor in governance, business, and in our everyday lives. It is expected that 2.75 billion people will be online by the end of 2013 [2].
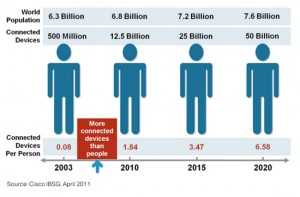
But it is not only people who immigrate into Neuland – it is also electronic devices. Around 12 billion media players, smartphones, TV sets and yes, even cars and smart meters are connected to the Internet today. By 2020, that number is expected to increase to 50 billion – that’s an impressive 6.6 devices per human being [3, p. 3].
One of the major driving factors of this trend is the so-called ‘Internet of Things’ (IoT). It refers to human-to-device or device-to-device communication over standard network protocols such as IP. In the context of IoT, a ‘thing’ is pretty much everything interacting with the Internet in one way or another. Especially sensors of all kinds play a crucial role in the Internet of Things: they monitor, collect, transmit, analyze and distribute the data that has become so vital for many a business [3, pp. 6]. Examples include building automation components (BAC), Personal Area Networks (PANs), temperature sensors and RFID tags [4, pp. 1]. In today’s digitized world, even a piece of clothing may come with a chip that talks IP.
When it comes to security, however, the true challenge is not someone’s networked television set, but a nation’s critical infrastructure (CI). Many vital systems rely on an uninterrupted Internet connection to maintain their working state. Power plants, financial services, telecommunications and transportation are only a few examples of critical infrastructure [5, pp. 27]. In general, CI equals a country’s most important assets – be it a physical facility or a computer system.
To give the reader an idea of just how ubiquitous and important the Internet has become, we incorporated a number of different attack scenarios into the story. The nameless hacker not only sabotages critical infrastructure but also causes mayhem in a wide range of civilian applications that affect everyone in equal measure.
[1] United Nations Office on Drugs and Crime, “Comprehensive Study on Cybercrime”, Draft, 2013.
[2] International Telecommunications Union, “Internet users per 100 inhabitants 2006-2013”, http://www.itu.int/en/ITU-D/Statistics/Documents/statistics/2012/ITU_Key_2006-2013_ICT_data.xls (accessed 2013/06/29), ITU Geneva, 2013.
[3] D. Evans, “The Internet of Things – How the Next Evolution of the Internet Is Changing Everything”, Cisco Internet Business Solutions Group, 2011.
[4] T. Heer et al., “Security Challenges in the IP-based Internet of Things”, RWTH Aachen University, 2011.
[5] Department of Homeland Security, “National Strategy for Homeland Security”, www.hsdl.org/?view&did=479633 (accessed 2013/06/27), DHS, 2007.



